Has your boss asked you to be more strategic? Are you unclear what that means? And when you ask them to define “strategy” do they say something vague like, “it’s a security plan aligned to business goals and objectives?” If this is your lot, and you’re still perplexed, then just know you are normal.
Let’s be honest, true strategic leadership is rare – particularly in security. It’s not for a lack of effort. It’s for a lack of specificity on what (and how) to strategize. This article intends to help – by starting with a movie.
A Winning Strategy In Action
The film Moneyball is a master-class example of aligning objectives, goals, strategy, and tactics. We’re going to apply it to security. That means you must eventually see the movie! Or even better, read the book. It’s subtitled, “The Art Of Winning An Unfair Game.”
The protagonist (the Oakland A’s) had the worst budget in major league baseball. It was a quarter the size of teams like the New York Yankees and the Boston Red Sox. But the A’s turned their meager budget into an advantage. Indeed, their financial constraints became the impetus for an industry-changing strategy based on arbitrage opportunities, which had winning the World Series as its objective.
The TL;DR on the A’s strategy:
- Objective: Win the World Series.
- Goal: Do it in one year with a quarter of the competition’s budget.
- Strategy: Buy undervalued assets.
- Tactics: Maximize walks and build superstars in the aggregate.
Constraints Drive Strategy
The A’s goal of winning with a paltry budget drove the need for a new strategy. That new strategy focused on buying undervalued assets. For example, players good at getting walks were not in high demand. Yet walks were strongly correlated with wins – stronger than getting runs. (The A’s economist discovered this.) And players that got walks were cheap. So the A’s started to buy them up.
A similar tactic was making superstars in the aggregate. The A’s sold off expensive assets, replacing them with inexpensive (often farm-league) players. Each player had an undervalued skill. Their combined salaries were less than the superstars they replaced – while their value in making wins was equivalent if not better.
| Understanding the Difference Between Strategy and Tactics for Effective ROI If you buy wins cheaply, then you have ROI. If you implement tactics disconnected from objectives, goals, and strategy then you simply buy cheap losses, or maybe you get lucky and win. But it was not a strategy; it was mere tactics. As Sun Tzu warned, “Tactics without strategy is the noise before defeat.” |
Moneyball Applied To Cyber
Let’s apply the Moneyball pattern to cybersecurity.
| A Resilience client in the distribution industry planned to expand their business to e-commerce. With this expansion came new revenue opportunities, as well as for cyber risk. The client’s Risk Manager had trouble determining how much insurance coverage they should purchase as peer benchmarks didn’t account for the complex nature of their large attack surface, and simple data breach calculators weren’t helpful. They purchased a policy with a $10M limit to protect their ability to deliver value. |
As I did above, I will start with a very high level Too Long; Didn’t Read (TL;DR) outline and then unpack each bullet. But my particular focus will be on one of the tactics – the Quantified Cyber Action Plan (Q-CAP) a new part of the Resilience Solution available to Edge clients.
The TL;DR Cyber Resilience Strategy
- Objective: Make the business resilient to plausible cyber losses
- Goal: Loss exceedance of $10M at 5% and $20M at 1% by 2024
- Strategy: Controls arbitrage and reserves assurance
- Tactics: Implement a Quantified Cyber Action Plan (Q-CAP)
The Cyber Resilient Objective
Cyber Resilience ensures the business thrives in the face of plausible losses. You don’t get that by simply following a security framework or buying solutions an analyst told you to. It’s more involved, as seen in the Cyber Resilience Domain infographic below. Cyber resilience in practice includes:
- Assessing relevant threats
- Assessing your value at risk (aka losses)
- Quantifying the likelihood of threats creating losses
- Quantifying the return on cross-cutting controls
- Quantifying ideal limits for risk transfer
- Quantifying capital reserves requirements for limit exceedance
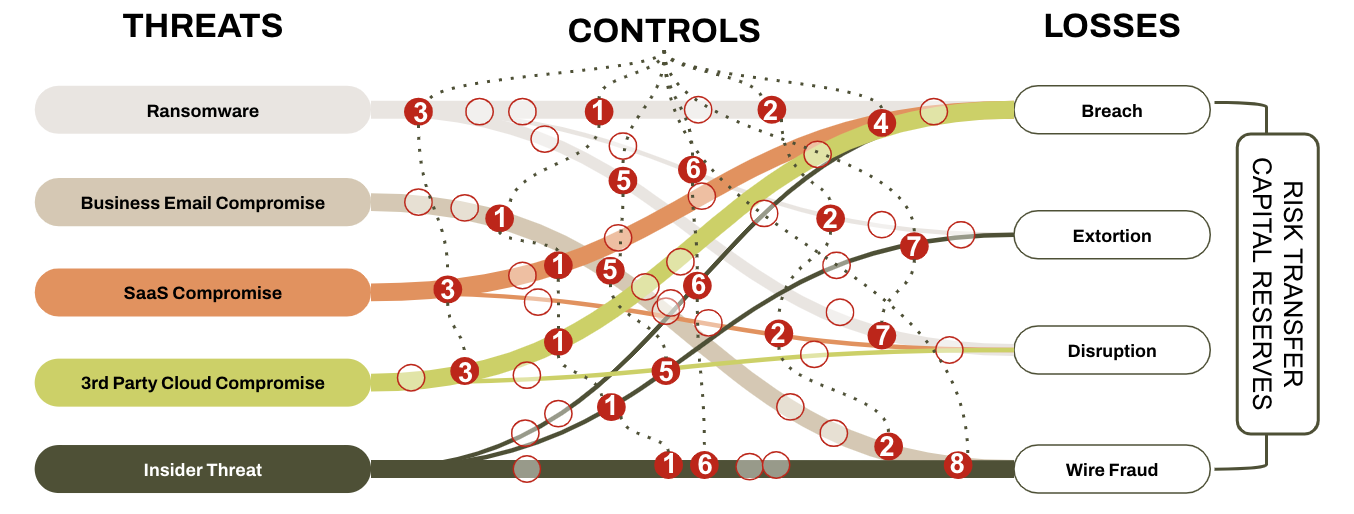
Figure 2 The Cyber Resilient Domain
| Note: Cyber Resilience requires security operations, finance, and risk management leaders to collaborate. Traditionally, these individuals operate in silos. They need a common language to communicate their challenges and align under a common goal – this language is dollars and cents. When we can talk in terms of dollars and cents, it’s easier to make a case to the money people. These are the people who designate the budgets that let us do our jobs, ie., executives, stakeholders, and Boards of Directors. Thus, cyber resilience must be considered a shared objective. |
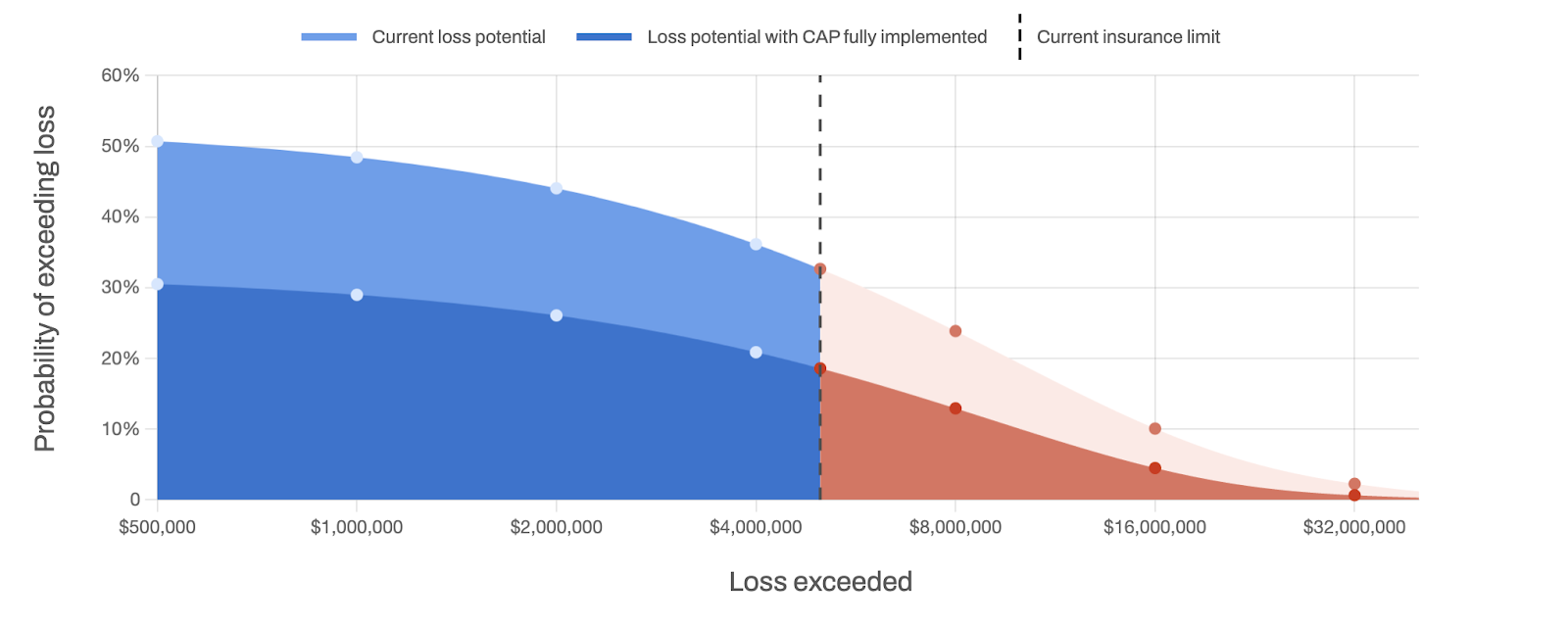
Figure 3 Q-Cap Loss Exceedance Curve
The Cyber Resilience Goal
A goal measures the objective. The above Loss Exceedance Curve was generated by our Q-CAP (Figure 3). It shows that our client has a ~33% chance of exceeding $5M in losses. Their new goal (represented by the lower curve) has a 5% chance of exceeding $10M. There’s also a tail exceedance goal of 1% for $20M.
The Cyber Resilience Strategy
A strategy is a qualitative explanation of how our client will achieve their goal. Before we clarify our strategy, let’s add some constraints. First, they can’t get more than $10M in limit. This is a function of substandard cyber hygiene. Also, their budget is fixed at less than $1M for new solutions. Given those constraints, I’m calling this strategy Controls Arbitrage and Reserve Assurance.
| Controls arbitrage does two things. First, it’s investing in cross-cutting high ROI controls. Cross-cutting is seen in Figure 2. For example, most of the controls are cross-cutting, spanning multiple threat and loss scenarios. Controls 4 and 8 stand alone. They may still have outsized ROI relative to the others, so they are not entirely out of the picture. Arbitrage occurs when recouping funds from low-ROI vendors and reinvesting in better (cross-cutting) bets. Reserve assurance validates the integrity of your treasury relative to plausible excess losses. Imagine your CFO is unsure if she has enough cash to backstop unexpected losses (the losses that exceed your insurance limits). In working with you, she decides she needs tail risk down to a 1% likelihood of exceeding $20M. And she expects that the possibility of exceeding $30M is negligible. This represents the CFO’s cyber risk tolerance relative to the integrity of her treasury. |
Cyber Resilience Tactics
Constructing a Quantified Cyber Action Plan or Q-CAP is the most pivotal tactic in building Cyber Resilience. The Q-CAP’s job is to rank order your spend on security controls. The ranking is based on a concept called return on controls (ROC). ROC considers how much losses the control reduces in relation to its cost. For example, you would have a 100% ROC if your control costs $100K and it removed $200K in losses.
Figure 3 above demonstrates how controls buy down risk. The light blue part of the curve shows where our client is now. If they choose to invest in the controls based on the Q-CAP, they can reduce risk to the dark blue area and extending into the dark red.
Looking closely at the curve, you will see that the recommended controls strategy, given the client’s budget, will not get them to their goal. This is where the arbitrage strategy comes in. Could they sell off the low ROC performers? What if they fail to meet your goal after everything is said and done? Meaning, could they exceed their risk tolerance?
This is where many play the “risk acceptance” card. The reality is that acceptance is just code for, “the CFO will pay it out of our reserves.” This client (or more likely their CFO) is participating in what we like to call, “structured worry.” It’s better than, “unstructured worry.” The latter is nothing more than not counting the cyber insurance costs, which is a form of moral hazard.
This is where resourcefulness and creativity kick in. Figure 2 indicates that breach risk is relatively outsized. The client would also know this through a value-at-risk assessment. Can the volume and exposure of regulated data be curtailed without cyber insurance costs? Is data being needlessly duplicated in SaaS environments? Or are there SaaS services that are not entirely necessary and simply be turned off?
This is only the tip of the iceberg in creativity and resourcefulness driven by a Cyber Resilient strategy that the Q-CAP supports.
Consider that Cyber Resilience isn’t merely an objective we use with our customers – its a comprehensive solution.
The Quantified Cyber Action Plan is a key component in The Resilience Solution, allowing our clients to generate a personalized (and ROI prioritized) cyber mitigation plan that meets industry standards and reduces the most loss at the lowest cost.
To learn more about the principles, practices, and platforms related to the QCAP, request a demo and follow Resilience on LinkedIn and Twitter for updates on educational resources, such as our free community webinar series that delves deeper into this topic.