One place to assess, measure, and manage your cyber risk.

The Resilience Solution has five integrated benefits
Financially-Proven AI Platform
Continuous learning system that creates clarity from cybersecurity visibility
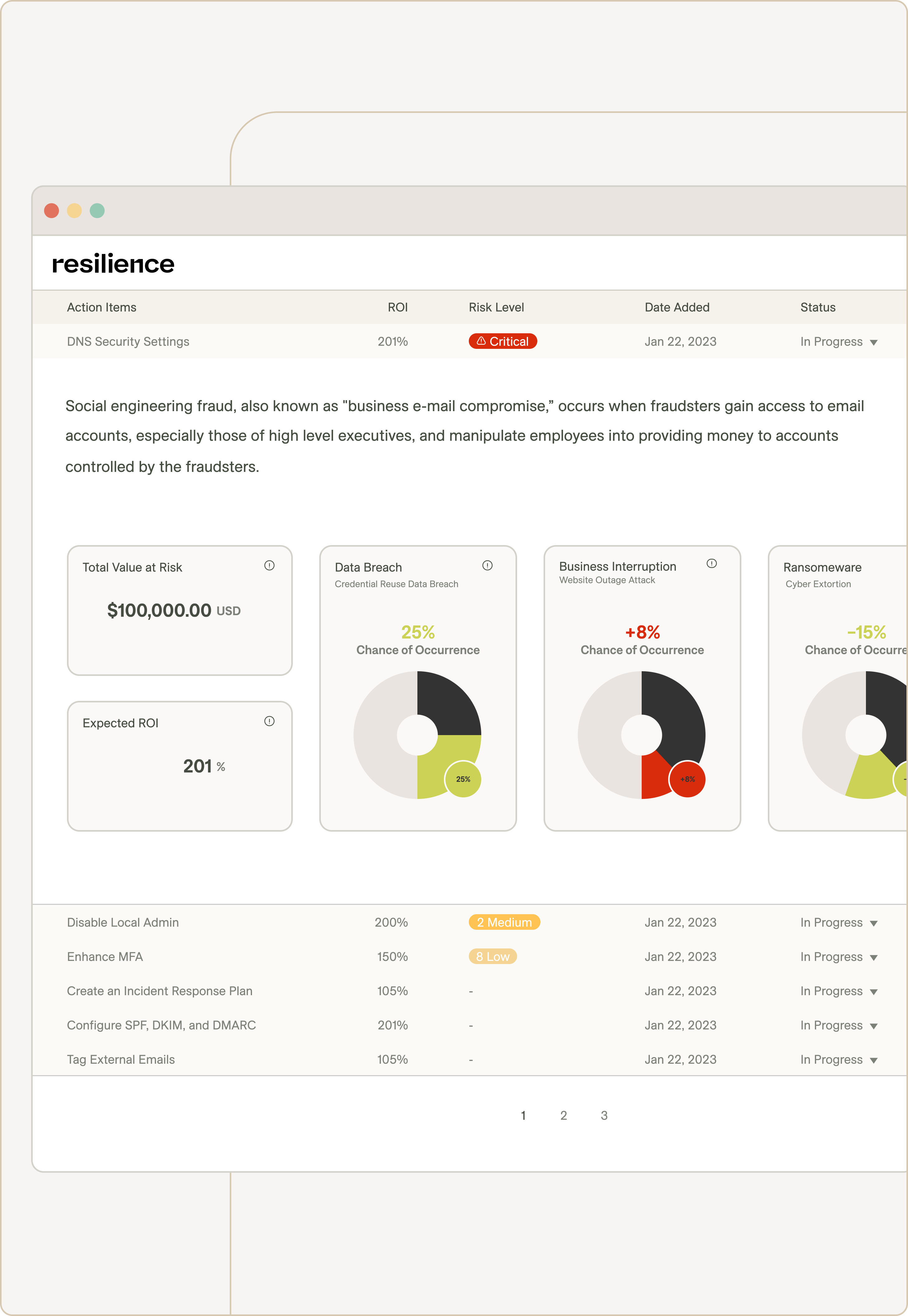
Quantified Action Plan
Prioritization and context for better & faster operational decision making
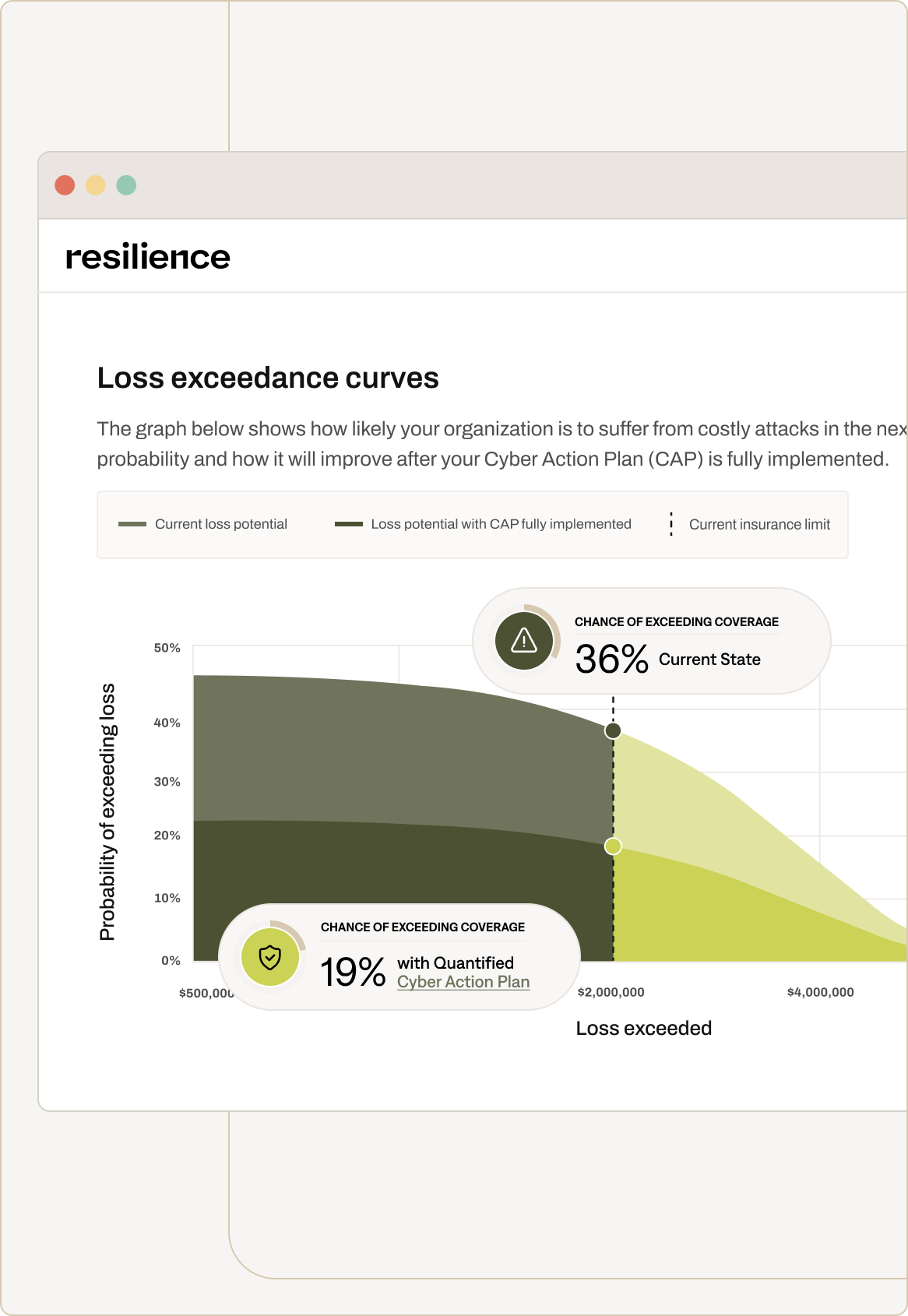
Responsive Policy
Comprehensive coverage, purpose-built for the dynamism & complexity of cyber
Human-in-the-Loop Partnership
Expert counsel to guide, validate, and augment your cyber risk team
Cyber Advocacy Program
Resources to activate an engaged community up & down your organization
Read More
Resilience Solution Packages
|
Ongoing visibility into external attack surface risk and dark web exposure analyzing over 180 signals
|
|
|
|
|
State-of-the-art probabilistic attack scenarios and quantification models to anticipate threat impact
|
|
|
|
|
Built-in interactivity to enable secure collaboration and accurate exposure validation
|
|
|
|
|
Continuously monitor Identity Access Management (IAM) for a multi-cloud environment
|
|
|
|
|
API-Integrated continuous risk assessment for internal & external attack surface
|
|
|
|
|
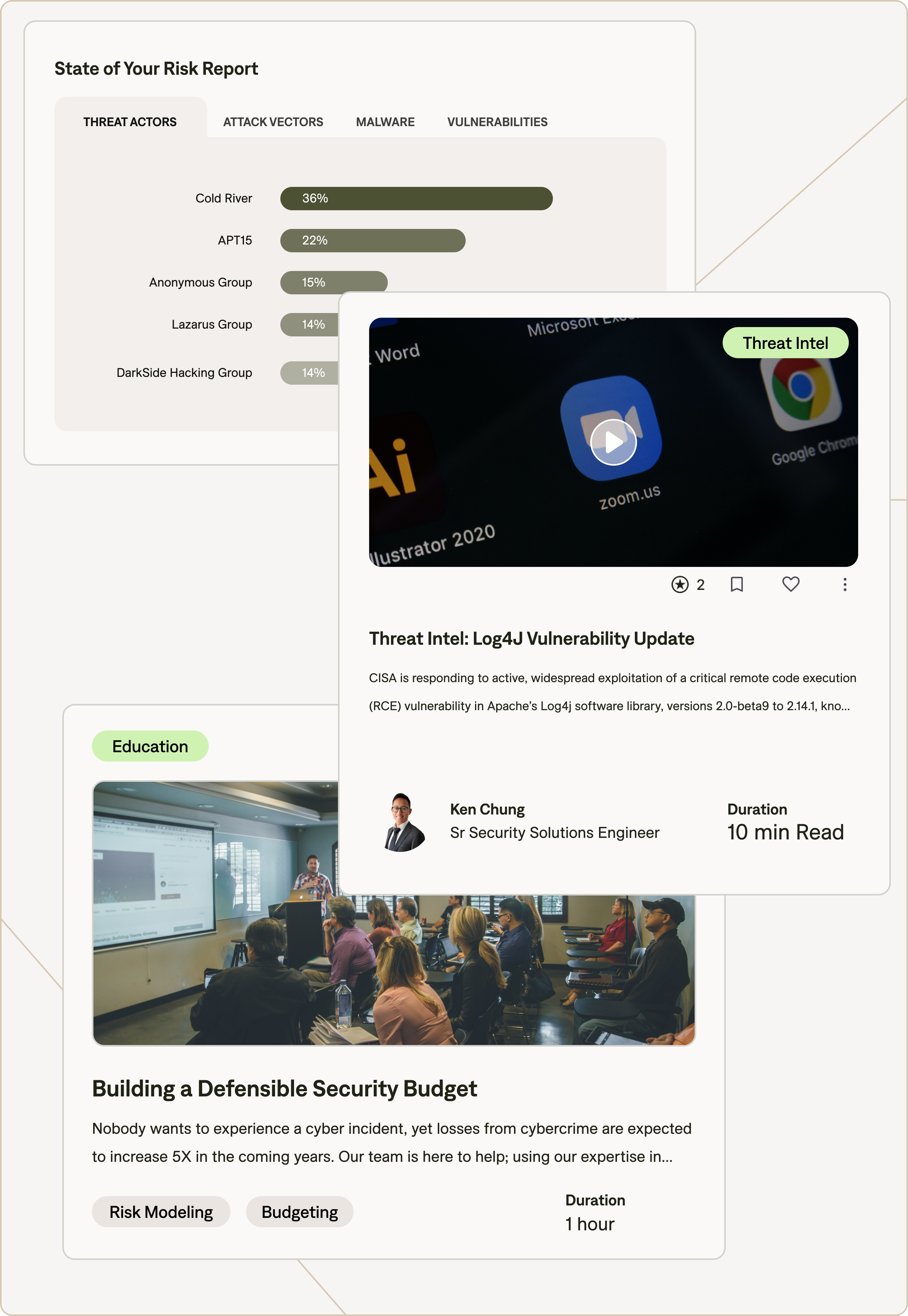
State of Your Risk Analysis summarizes and quantifies your comprehensive cyber risk profile
|
|
|
|
|
Access to Virtual Training: How to Build a Defensible Cybersecurity Budget
|
|
|
|
|
ROI-prioritized Risk Mitigation Plan to translate cybersecurity controls and threats to financial risk
|
|
|
|
|
State of Your Vendor Risk Analysis summarizes the cyber risk profile of up to 15 vendors
|
|
|
|
|
Holistic third-party vendor risk assessment for up to 100 vendors
|
|
|
|
|
Streamlined & comprehensive policy that covers costs, loss, and liability
|
|
|
|
|
Easy access to policy documents and recommendations via our digital portal
|
|
|
|
|
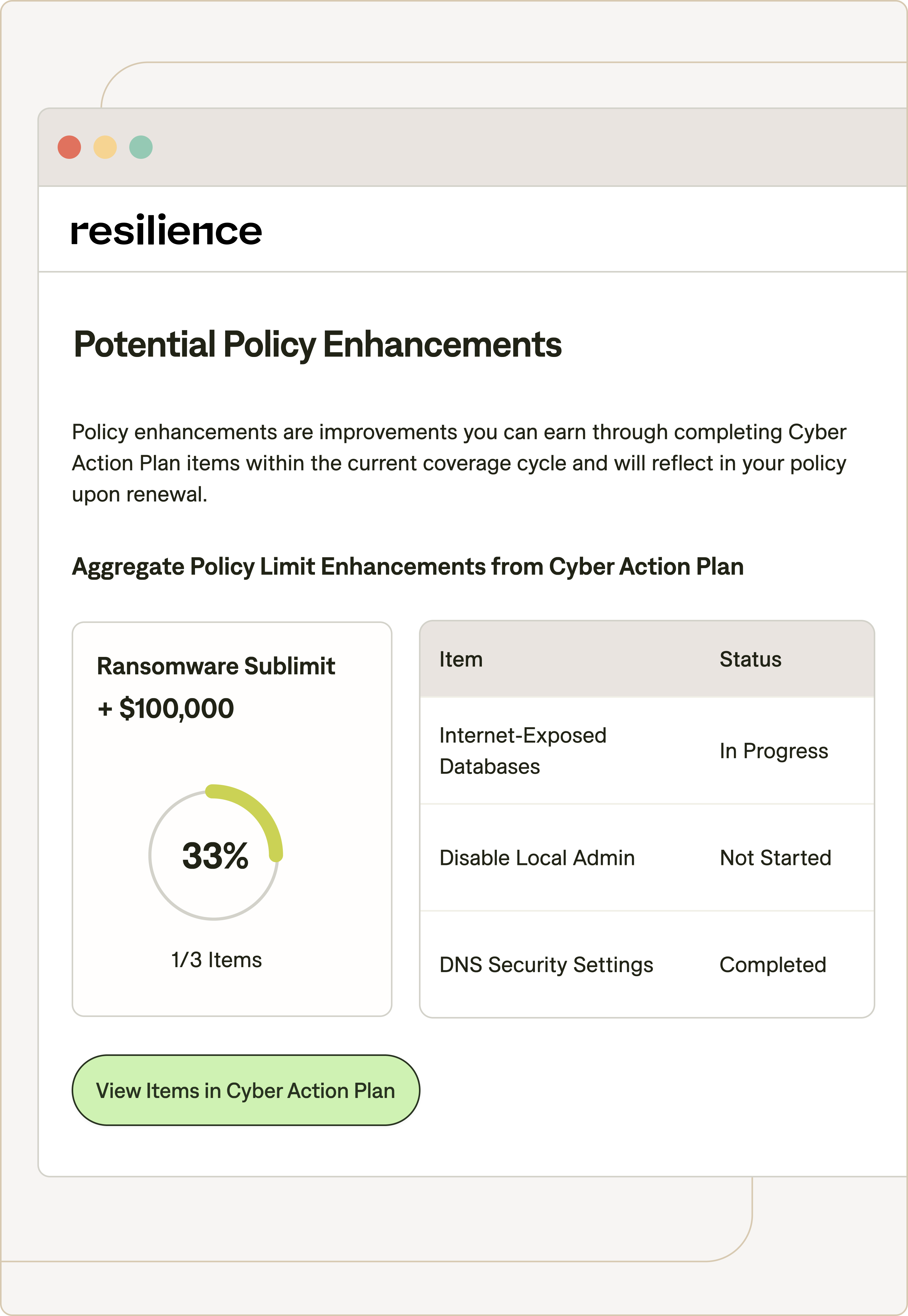
Improved coverage, limits, and retention at mid-term based on ongoing engagement
|
|
|
|
|
Hassle-free renewal that bypasses long-form applications
|
|
|
|
|
Dynamic risk transfer for your evolving risk posture
|
|
|
|
|
Expert-triaged threat alerts personalized and prioritized for individual business attributes
|
|
|
|
|
In-house claims & incident management available 24/7
|
|
|
|
|
Annual in-depth tabletop exercise tailored to your organization’s risk operations
|
|
|
|
|
Quarterly meetings with industry-leading cybersecurity and cyber risk experts
|
|
|
|
|
Industry-first Cyber Risk Modeling Lab for scenario and investment planning
|
|
|
|
|
Best practices and “how to” cyber risk management guides
|
|
|
|
|
Incident response and lifecycle management plan for review and validation
|
|
|
|
|
Comprehensive Cyber Risk reporting for executives and board members
|
|
|
|
|
Actionable cyber governance standards tailored from Cyber Risk best practices
|
|
|
|
|
Advisory services with industry-leading cybersecurity and risk engineers
|
|
|
|
Financially-proven AI platform creates clarity from cybersecurity visibility

Ongoing visibility into external attack surface risk and dark web exposure analyzing over 180 signals
State-of-the-art probabilistic attack scenarios and quantification models to anticipate threat impact
Quantified action plan for better and faster operational decision making

State of Your Risk Analysis summarizes and quantifies your comprehensive cyber risk profile
Access to Virtual Training: How to Build a Defensible Cybersecurity Budget
Responsive policy for coverage purpose-built for the complexity of cyber

Streamlined & comprehensive policy that covers costs, loss, and liability
Easy access to policy documents and recommendations via our digital portal
Human in the loop partnership to guide and augment your cyber risk team

Expert-triaged threat alerts personalized and prioritized for individual business attributes
In-house claims & incident management available 24/7
Cyber Advocacy Program resources to engage your organization

Best practices and “how to” cyber risk management guides
Incident response and lifecycle management plan for review and validation
Financially-proven AI platform creates clarity from cybersecurity visibility

Ongoing visibility into external attack surface risk and dark web exposure analyzing over 180 signals
State-of-the-art probabilistic attack scenarios and quantification models to anticipate threat impact
Built-in interactivity to enable secure collaboration and accurate exposure validation
Continuously monitor Identity Access Management (IAM) for a multi-cloud environment
Quantified action plan for better and faster operational decision making

State of Your Risk Analysis summarizes and quantifies your comprehensive cyber risk profile
Access to Virtual Training: How to Build a Defensible Cybersecurity Budget
ROI-prioritized Risk Mitigation Plan to translate cybersecurity controls and threats to financial risk
State of Your Vendor Risk Analysis summarizes the cyber risk profile of up to 15 vendors
Responsive policy for coverage purpose-built for the complexity of cyber

Streamlined & comprehensive policy that covers costs, loss, and liability
Easy access to policy documents and recommendations via our digital portal
Improved coverage, limits, and retention at mid-term based on ongoing engagement
Hassle-free renewal that bypasses long-form applications
Human in the loop partnership to guide and augment your cyber risk team

Expert-triaged threat alerts personalized and prioritized for individual business attributes
In-house claims & incident management available 24/7
Annual in-depth tabletop exercise tailored to your organization’s risk operations
Quarterly meetings with industry-leading cybersecurity and cyber risk experts
Cyber Advocacy Program resources to engage your organization

Best practices and “how to” cyber risk management guides
Incident response and lifecycle management plan for review and validation
Comprehensive Cyber Risk reporting for executives and board members
Actionable cyber governance standards tailored from Cyber Risk best practices
Financially-proven AI platform creates clarity from cybersecurity visibility

Ongoing visibility into external attack surface risk and dark web exposure analyzing over 180 signals
State-of-the-art probabilistic attack scenarios and quantification models to anticipate threat impact
Built-in interactivity to enable secure collaboration and accurate exposure validation
Continuously monitor Identity Access Management (IAM) for a multi-cloud environment
API-Integrated continuous risk assessment for internal & external attack surface
Quantified action plan for better and faster operational decision making

State of Your Risk Analysis summarizes and quantifies your comprehensive cyber risk profile
Access to Virtual Training: How to Build a Defensible Cybersecurity Budget
ROI-prioritized Risk Mitigation Plan to translate cybersecurity controls and threats to financial risk
State of Your Vendor Risk Analysis summarizes the cyber risk profile of up to 15 vendors
Holistic third-party vendor risk assessment for up to 100 vendors
Responsive policy for coverage purpose-built for the complexity of cyber

Streamlined & comprehensive policy that covers costs, loss, and liability
Easy access to policy documents and recommendations via our digital portal
Improved coverage, limits, and retention at mid-term based on ongoing engagement
Hassle-free renewal that bypasses long-form applications
Dynamic risk transfer for your evolving risk posture
Human in the loop partnership to guide and augment your cyber risk team

Expert-triaged threat alerts personalized and prioritized for individual business attributes
In-house claims & incident management available 24/7
Annual in-depth tabletop exercise tailored to your organization’s risk operations
Quarterly meetings with industry-leading cybersecurity and cyber risk experts
Industry-first Cyber Risk Modeling Lab for scenario and investment planning
Cyber Advocacy Program resources to engage your organization

Best practices and “how to” cyber risk management guides
Incident response and lifecycle management plan for review and validation
Comprehensive Cyber Risk reporting for executives and board members
Actionable cyber governance standards tailored from Cyber Risk best practices
Advisory services with industry-leading cybersecurity and risk engineers
Frequently Asked Questions
What is Cyber Resilience?
Cyber Resilience focuses on quantifying cyber exposure and prioritizing strategic objectives that matter most to limiting financial loss from a cyber incident. As opposed to traditional cybersecurity approaches, cyber resilience focuses on how business opportunity and risk mitigation work together and support making informed trade-offs when necessary. We have seen how these alignment of objectives can help organizations greatly reduce to exposure to extortion attempts and reduce total costs of incidents when implemented correctly.
How does Resilience provide visibility into the client’s cyber risk?
The Resilience Solution utilizes over 180 data signals to offer clients a comprehensive risk assessment, including external attack surface exposure and self-reported information. In addition, Resilience offers continuous cyber risk assessment by integrating with 3rd party cloud services through APIs, resulting in faster and more accurate risk analysis.
How is this different from our current Cyber Primary Care (CPC)?
We’ve included elements from our CPC offering with the Essential Package to provide additional value to our entire customer base beyond our core insurance policy. All of our Essential customers will continue to have access to expert-triaged threat alerts, a best-in-class in-house claims and incident management team, and a streamlined and comprehensive insurance policy.
Our new Edge Package is everything you already know and love about CPC (includes everything in our Essential package), taken to the next level. This integrated cyber risk management offering helps connect CISOs, risk managers, and CFOs, allowing them to be integrated and efficient as they work to quantify their risk and prioritize investments.
The Enterprise Package includes everything in Edge plus enhanced leverage of Resilience proprietary cyber risk quantification models and bespoke risk modeling development services to assist organizations with their risk assessment, forecasting, and mitigation needs – developed as a bespoke solution for clients.
What does the cyber risk solution cost?
We are pleased to offer our clients the Essential Package at no extra charge from their insurance premium. Additionally, we offer advanced cyber risk management services through our Edge and Enterprise packages, which require an annual fee to access. These premium offerings provide exceptional value and are not included in the base package.
How difficult is this to roll out?
Resilience experts want to make this process seamless for you and your team, which is why we are available to help every step of the way. We offer comprehensive onboarding for key stakeholders, regular engagements to help enact your cyber hygiene plan, and more.
Do I really need a cyber resilience solution?
In today’s highly digital environment, building resilience against cyber threats is paramount to business success. Cyber insurance and security are no longer effective when working in silos. Connecting advanced cybersecurity visibility to enhanced and modular insurance policies via actionable cyber hygiene strategies is the strongest way to combat the complexities of cyber risk.
Can Resilience help in an emergency?
Absolutely. Our in-house claims team is available 24/7 to handle any of our clients’ cyber emergencies. If you are experiencing an incident, 1-(302) 722-7236.