“Chance favors the prepared mind.” – Louis Pasteur.
The month of December is full of gifts! One ‘gift’ that has many organizations doubling down on their end-of-year cyber risk management is the new SEC Cyber Rules, which go live this month on December 18th. To go along with this, Resilience has an early present for you.
Our last webinar in the “How To Build A Defensible Security Budget” series aired December 2023. If you are concerned about the new SEC rules, then our final topic is a must-watch. Many of the principles of cyber resilience covered in our webinar line up well with the new expectations of the SEC. Here is one key principle for starters:
Cyber Resilience Makes Your Risk-Surface Visible So It Can Be Managed
The new rules…require registrants to describe their processes, if any, for assessing, identifying, and managing material risks from cybersecurity threats, as well as the material effects… – SEC Press Release Rules on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure by Public Companies.
What does this have to do with a defensible cybersecurity budget?” In our very first webinar (nearly 10 months ago), we stated that our objective was to make enterprises “Resilient To Material Loss.” Resilient organizations plan to fulfill their commitments to stakeholders in the face of material losses. And they are transparent about material risks.
That transparency is input to the defensible budget. The defensible budget becomes the dynamic plan for resilience. And we believe it’s a plan that can aid you in assessing material risk and thus being responsible for material loss.
This article will focus on the principles of cyber resilience that support the budget process and lead to an organization being resilient.
5 Principles Of Cyber Resilience
What is a principle? A useful definition is, “one of the fundamental tenets or doctrines of a system, a law or truth on which others are founded.” This definition is from the 16th century – and it works here.
In this article, we expound on the fundamental tenets of a cyber-resilient system. Those tenets distinguish it from mere cybersecurity. And it is from these tenets (or truths) that the cyber resilient organization operates.
- Cyber Resilience tolerates losses – within limits
- Cyber Resilience connects security and risk transfer – avoiding silos
- Cyber Resilience seeks capital efficiency – while preventing negligence
- Cyber Resilience makes your risk surface visible – so it can be managed
- Cyber Resilience incentivizes cyber hygiene – by maximizing Return On Controls (RoC)
Cyber Resilience tolerates losses – within limits.
This is different from implicit cybersecurity principles, which seek complete loss elimination as an end goal. The CFO, CRO, and CISO determine what the business can stand to lose. Considerations include some amount of losses from breaches, business disruption, wire fraud, extortion, etc. It’s a first step in defining risk tolerance. Setting an insurance limit is the second step.
Your limit expresses how much financial coverage you can expect in the event of a material loss. It’s a mathematically unambiguous and contractually binding expression of tolerance. Limits also serve another essential function.
Limits demark where risk stops being transferred away from capital reserves. Of course, some impact on capital reserves is tolerable, but excess losses are intolerable. Defining how much impact is acceptable is the third step in defining tolerance. Ensuring capital reserves (aka the treasury) can backstop excess losses is the CFO’s domain. That’s, in part, why many CFOs are also insurance buyers. Now that we understand what we are protecting (capital reserves), we can ask if it’s actually protected.
How does the CFO Fit into Cyber Resilience?
What if the CFO finds out that there is a 10% chance of exceeding a combined limit of $100 million over a three-year period? Additionally, what if there is a 5% tail risk of exceeding $300 million in losses over that same time frame? If the CFO feels the treasury is overexposed – particularly given other potential business opportunities, commitments, and threats – then a change must be considered. As you can see, this is not a solo act. Our trio of leaders must collaborate.
Together, they may want to say something like, “With our value-at-risk and state of controls, we believe a 4% chance of exceeding $80 million and a 1% chance of losing $150 million is acceptable. We are going to put together an insurance and cyber strategy to meet this goal.”
Cyber Resilience connects security with insurance – avoiding silos.
Security investments mitigate risk by reducing the likelihood of experiencing a material loss. Once you have actually incurred a material loss, insurance kicks in.
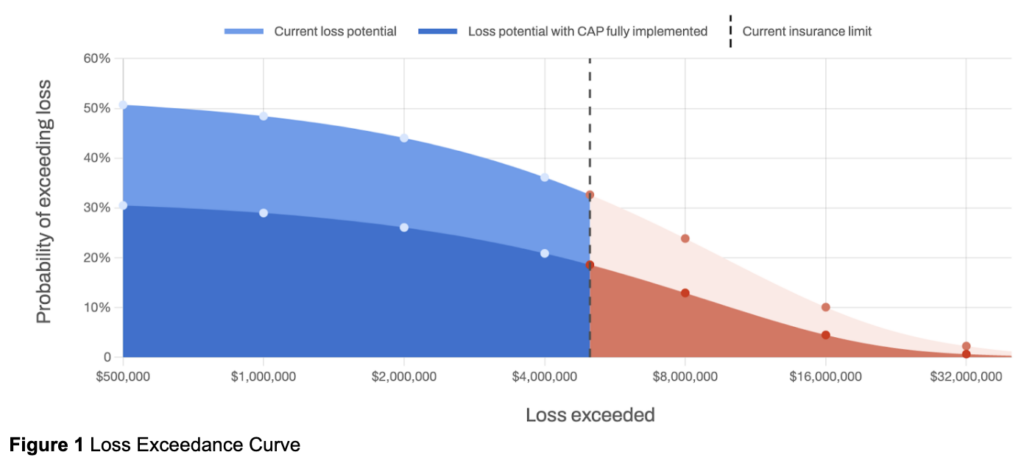
Graphically, we would say security investments buy (or push) risk downward. In the Loss Exceedance Curve in Figure 1, security investments impact the y-axis marked as the “Probability Of Exceeding Loss.” That is what we referenced in our CFO discussion above – when discussing the chance of exceeding some dollar amount.
Think of security as a downward motion while risk transfer moves the limit from left to right. In the image above, the limit is the dotted line on the x-axis at about $5 million.
Mitigation and transfer, in effect, work like the dials on an etch-a-sketch to bring risk within tolerance. Here is the challenge: getting the transfer you want is largely dependent on the state of your security controls. If your controls are not strong enough relative to your assessed risk, you will have trouble getting the insurance level (and price) you want. In fact, you may not be able to get insurance at all.
Given this intertwined challenge, we conclude that security controls cannot be considered independently from transfer or from protecting capital reserves. The CISO, CFO, and CRO must work together through a shared “Cyber Resilient Objective,” with a quantitative goal of keeping risk within tolerance.
Cyber Resilience seeks capital efficiency – while preventing negligence
Over or under-investing in protection leads to distraction — or worse. The former takes needed capital away from important business opportunities. The latter (negligence) threatens the business with outsized losses.
After assessing value-at-risk, Resilience optimizes dollars spent on mitigations. It’s a method of prioritizing controls based on how efficiently they reduce the likelihood of loss in relation to cost. Formally, we call it “return on controls” (RoC). Controls are rank-ordered for deployment based on their returns and available budget. It’s capital efficiency that simultaneously avoids negligence. It achieves this outcome by targeting the reduction of plausible material losses at the lowest cost.
Insurance limits are then set with residual risk. That is the risk left after controls are implemented. As stated, the CFO wants a limit that will reduce the impact on their capital reserves. And they want to reduce the magnitude of losses beyond their limit. Combinations of each are optimized to reduce both cost and impact.
Minimizing the Risk-Surface: Boosting Cybersecurity through Cyber Resilience
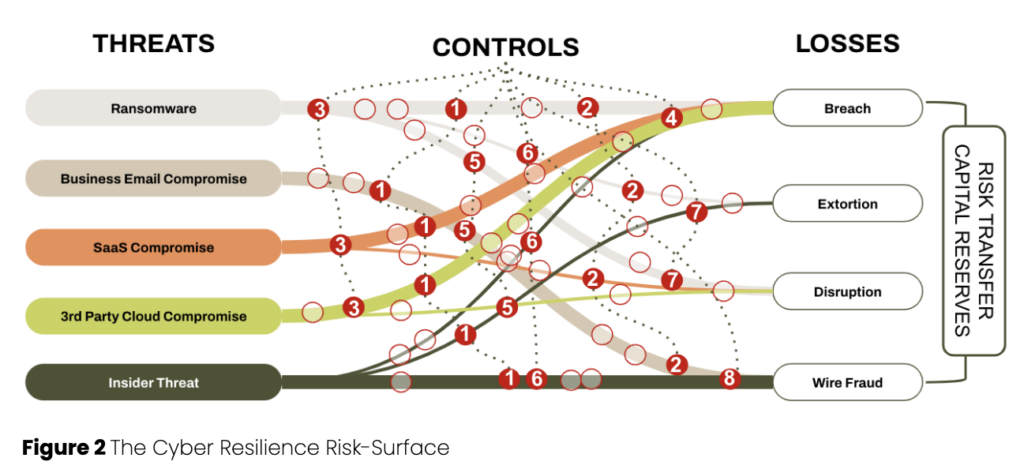
Risk-surface, as seen in Figure 2, considers the relationship between threats and losses. That relationship, when mapped out and quantified, represents a company’s value-at-risk. When value-at-risk is compromised, it leads to material loss.
Security controls reduce the likelihood of experiencing material losses. Risk transfer reduces the impact of material losses. And capital reserves backstop risk that may exceed insurance limits. All of this together is your risk surface.
The goal of monitoring your risk surface is keeping risk within tolerance. It is similar (in function) to traditional threat intelligence. That means there can be alerts for zero days, organized crime, state-sponsored attacks, etc. But cyber resilience-based visibility goes far beyond mere tactical security operations.
You first monitor your risk surface for changes in value-at-risk. Has it increased in volume? Were there changes in controls that made value-at-risk more exposed to threats? Exposed value-at-risk can qualify as material risk. Will excessively exposed material risk eclipse your risk tolerance? If so, what is the most efficient means of bringing risk back within tolerance? That will be a combination of tradeoffs between controls, limits, and capital reserves.
Cyber Resilience incentivizes cyber hygiene – by maximizing ROI.
What is good cyber hygiene? It’s security controls that target material risk. It is also controls that meet accepted and expected industry standards.
As mentioned above, control acquisition and rollout are ordered based on return on investment. High ROI controls (aka RoC) reduce the most loss at the lowest cost. Maximizing RoC allows for more controls spread across more risks, leading to better cyber hygiene.
The most efficient controls are cross-cutting. You can see an example of this in Figure 2. Control number 1 is cross-cutting. And when we say control, in this case, we mean “strategic control initiative” or “strategic security initiative.” An example of a strategic security initiative could be zero-trust architecture. That initiative is composed of a number of things like MFA, PAM, Federated Identity, etc., and may have the most value in reducing material risk relative to cost. Other initiatives then follow based on their returns.
Achieve Cyber Resilience by applying controls & limits for effective risk management
The infographic below is a loss exceedance curve. It is a compressed expression of cyber resilience. The current state, shown as a lime green curve, is the state of risk before controls. Your defensible budget recommends a set of control initiatives that bring that curve down to the target – orange line.
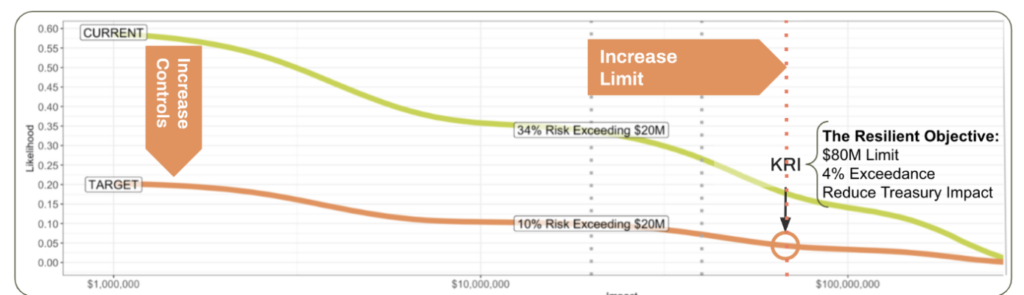
The next question concerns the limit. Is the current state of risk transfer (limit) adequate? Without controls changes, there is a relatively high likelihood of exceeding the limit. Is the magnitude of material losses that exceed the current limit intolerable? What about after control? Specifically, is a 10% chance of exceeding $20M something to get out of bed for? (Risk is relative. That means you need to decide.)
What if you could arrange controls and limits so you get a 4% chance of exceeding $80M while the likelihood of exceeding $150M is ~1%? If the cost of that plan has orders of magnitude efficiency over plausible material losses, then it becomes the goal. That assumes risk would be within business risk tolerance given capital reserves.
This is cyber resilience in action. It requires a clear objective, enhanced leadership, and increasingly quantitative and economically minded practitioners. All of that is ideally supported by a set of integrated solutions and tools that monitor risk-surface. The cyber-resilient organization continuously monitors for and responds to cyber risk that may become intolerable – and executes workflow to bring risk back into tolerance.
The cyber-resilient organization leverages dedicated solutions, tools, and teams that work together to make the business resilient to material losses to stay focused on its mission of delivering value to stakeholders.
Ready to fortify your organization’s cyber resilience? Request a demo of our comprehensive resilience solutions today and see how we can help you effectively manage and mitigate cyber risks. Don’t leave your organization vulnerable – take proactive steps towards building a resilient future.